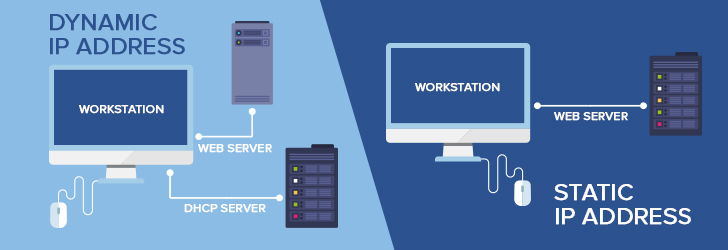
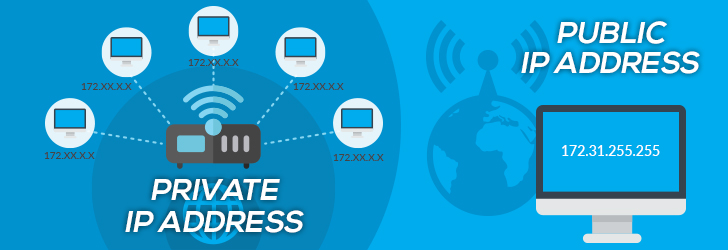
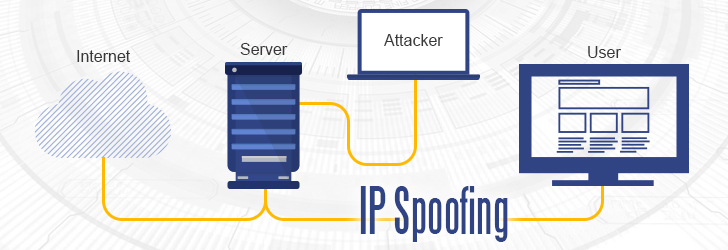
Internet Protocol Version 6 (or IPv6) is a successor of IPv4 Address standard developed by IETF, which is designed to solve IPv4 address exhaustion problem. IPv4 uses a 32-bit numbering scheme to represent an IP address, which has an address space of 232 or 4.3 billion. IPv6, on the other hand, uses a 128-bit numbering scheme (2128) which has big enough address space for many decades to come. IPv6 is intended to replace the IPv4, but the introduction of the CIDR (Classless Inter-Domain Routing) allocation scheme in 1993 within the IPv4 prolonged lifespan of IPv4 Addresses. With the anticipation of smartphones, tablets, smart appliances, and other electronic devices joining the Internet every day, IPv4 address space will eventually exhaust. As of May 2014 per Google Statistics, 96% of Internet traffic is IPv4 and only 4% is represented by IPv6. IPv4 and IPv6 are not interoperable by design, so the transition from IPv4 to IPv6 requires a "transition mechanism" such as Stateless IP/ICMP Translation, Transport Relay, 6rd, and other IPv6 transition mechanisms to make them interoperable.